Use WordPress as your OAuth 2.0 Server. Supports Single Sign On and other OAuth 2.0 features. FREE Setup and Support.
| Author: | miniOrange (profile at wordpress.org) |
| WordPress version required: | 4.8 |
| WordPress version tested: | 6.4.3 |
| Plugin version: | 6.0.5 |
| Added to WordPress repository: | 16-06-2017 |
| Last updated: | 20-03-2024 |
| Rating, %: | 98 |
| Rated by: | 38 |
| Plugin URI: | https://www.miniorange.com |
| Total downloads: | 32 731 |
| Active installs: | 700+ |
 Click to start download |
|
WP OAuth Server plugin turns your WordPress site into an OAuth Server. It allows you to login into Rocket Chat, Invision Community, WordPress, Odoo, EasyGenerator, Salesforce, Zapier, Moodle, ServiceNow, Edunext, Wickr, Freshdesk, FreshWorks, ServiceNow, ShinyProxy, Knack database, Circle.so, Tribe.so, Tribe, Mobilize, Nextcloud, Church Online, iSpring LMS, Academy of Mine, BoardEffect, TalentLMS, Laravel, PowerSchool, PowerSchool, Joomla, HubSpot, Shopify, MeritHub, Bookstack, Pimcore, 360 Learning, EventMobi, Synology, Drupal, Piano Analytics, Zerotier, and any other OAuth 2.0 compliant applications using WordPress credentials.
| WordPress OAuth Server Setup Guides | API Documentation | Demo / Trial |
You can checkout the below video tutorial to know how to setup SSO with your OAuth/OpenID Compliant Applications.
Basically, the OAuth Server plugin allows users to login into applications that are OAuth 2.0 compliant, using their WordPress login credentials. As it’s name suggests, it follows the OAuth 2.0 protocol. Along with that, it also supports OpenID Connect (OIDC), and JWT protocols.
The primary goal of the OAuth Server plugin is to enable Single Sign On so that users do not need to remember username and password for each application.
Once Single Sign On is enabled, users do not need to store sensitive information to login into different applications.
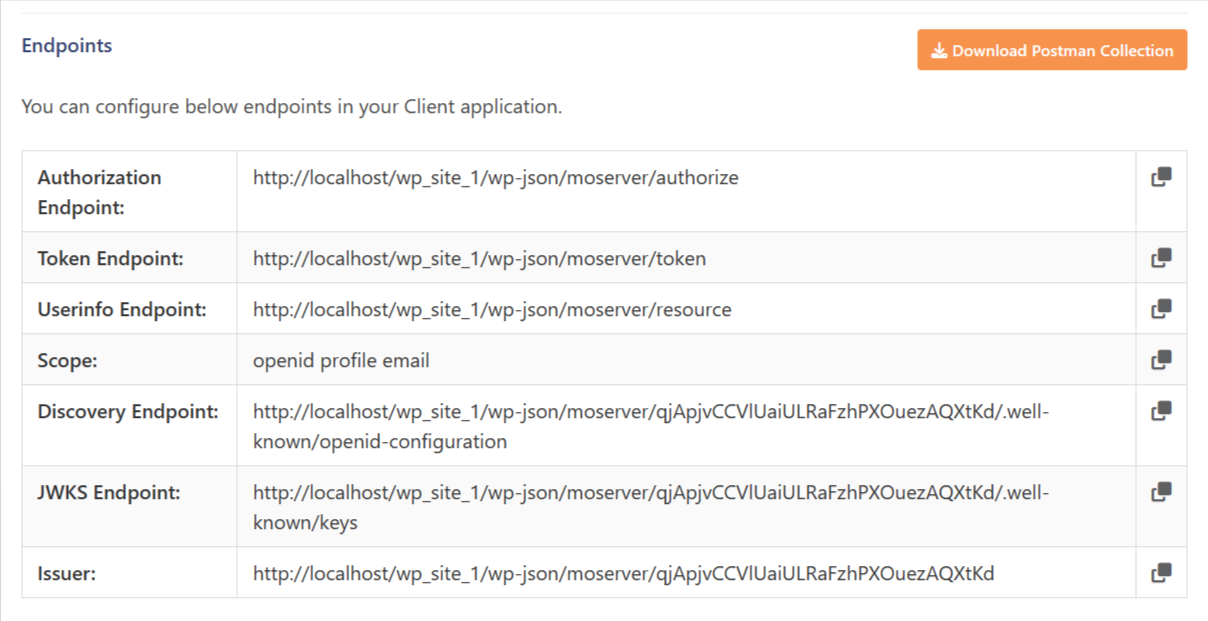
Discovery URL
The discovery url / well-known endpoint can be used to get metadata about your Identity Server. It will return information about the OAuth/OpenID endpoints, issuer URL, supported grant types, supported scopes, key material along with claims in the JSON format. These details can be used by the clients to create an OpenID server request. The well known configuration URL is accessible via /.well-known/openid-configuration, in relation to the issuer URL.
JWT Token Verification
JWT signing enables the token’s recipient to confirm that the token actually received includes all of the information encoded by the issuer in its original, unaltered form.
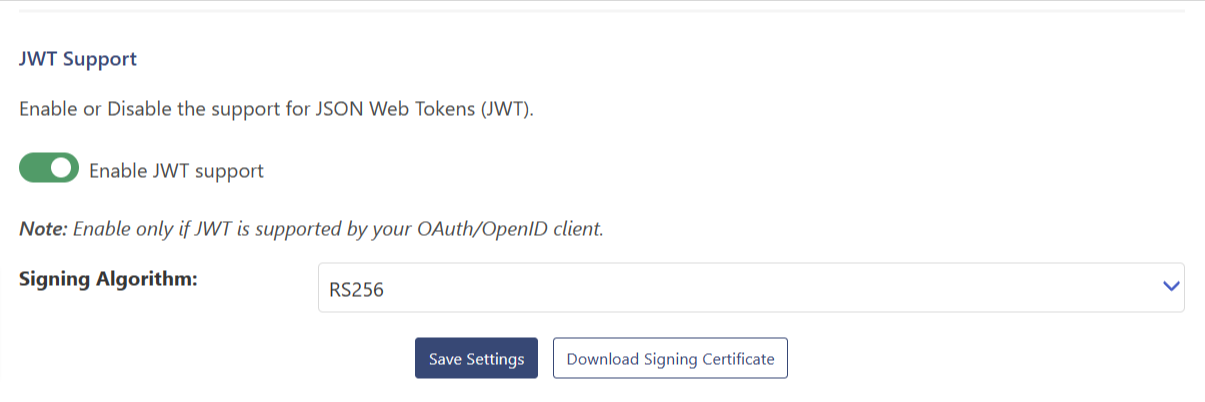
HS256, a symmetric signature algorithm, indicates that the signature is generated and verified using the same secret key. It is supported in the free version of the plugin.
RS256, an asymmetric signature algorithm is different from a symmetric algorithm in that a pair of private and public keys is used to sign and validate the data respectively instead of a single secret key.
Why RSA algorithm should be used?
The use of a public and private key pair makes RS256 more secure in comparison to HS256 where the public key is shared and might be compromised whereas in RS256, even if you do not have the control over your client, your data remains secure as it is signed using a private key. The premium version of the plugin supports the RS256 algorithm.
Postman collection
Postman collection JSON is a file that can be used for testing the configuration of OAuth 2.0 flow in the WP OAuth Server plugin without configuring an external OAuth Client by generating the access token and the API call to the resource endpoint subsequently.
LIST OF POPULAR OAUTH CLIENTS SUPPORTED
- Rocket.Chat
- Invision Community (IPB Forum)
- Odoo
- WordPress
- EasyGenerator
- Salesforce
- Zapier
- Moodle
- Edunext
- Wickr
- Freshdesk
- FreshWorks
- ServiceNow
- Knack database
- Circle.so
- Tribe.so
- Mobilize
- Nextcloud
- iSpring LMS
- Church Online
- Academy of Mine
- BoardEffect
- Laravel
- PowerSchool
- Joomla
- HubSpot
- Shopify
- MeritHub
- Bookstack
- Pimcore
- 360 Learning
- EventMobi
- Synology
- Drupal
- Piano Analytics
- Zerotier
WORDPRESS OAUTH / OPENID CONNECT SERVER USE CASES
- If you want to use your WordPress site as an Identity Server / OAuth Server / OAuth Provider and use WordPress user’s login credentials to login into your client site / application then you can use this plugin. You can also decide what kind of User data / attributes you want to send while Single Sign On into your client site / application.
- If you want to login to your Mobile app / Single Page web app (SPA) using your WordPress credentials, then you can use the Authorization code with PKCE flow grant type to achieve your use case.
- Single set of credentials will be used to login to multiple WordPress websites.
- You can access the NGINX resources using NGINX Authentication. Once you login into your client application using WP OAuth Server credentials, you will get JWT. Your client application can further use it for NGINX Authentication.
- Membership sync or role mapping is used to sync the memberships or roles assigned to your users from OAuth Server to OAuth/OpenID Client.
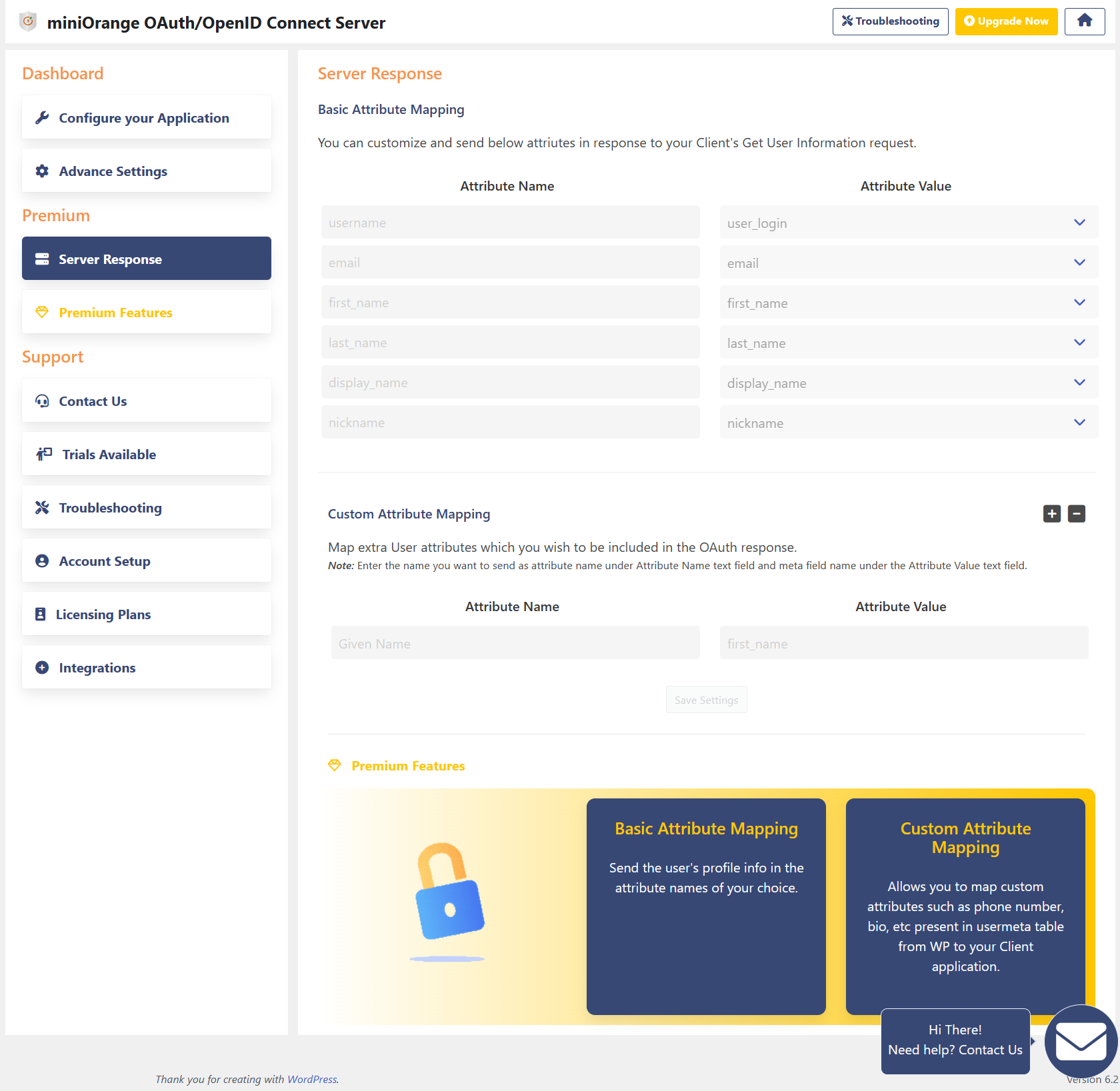
- Custom Attribute Mapping is useful if you want to send any additional attributes (other than the default ones) from your WordPress usermeta table to your OAuth/OpenID Client.
WORDPRESS OAUTH / OPENID CONNECT SERVER FREE VERSION FEATURES
- Supports Login with WordPress for Single Client application
- Protocol Support: OAuth 2.0, OpenID Connect (OIDC)
- Discovery document / well-known endpoint for automatic configuration
- JWT signing using HS256 or RS256 algorithm (Note: In RS256 algorithm, the keys will be common for all the free version installations)
- Postman collection for testing OAuth 2.0 flow without actually configuring the client application
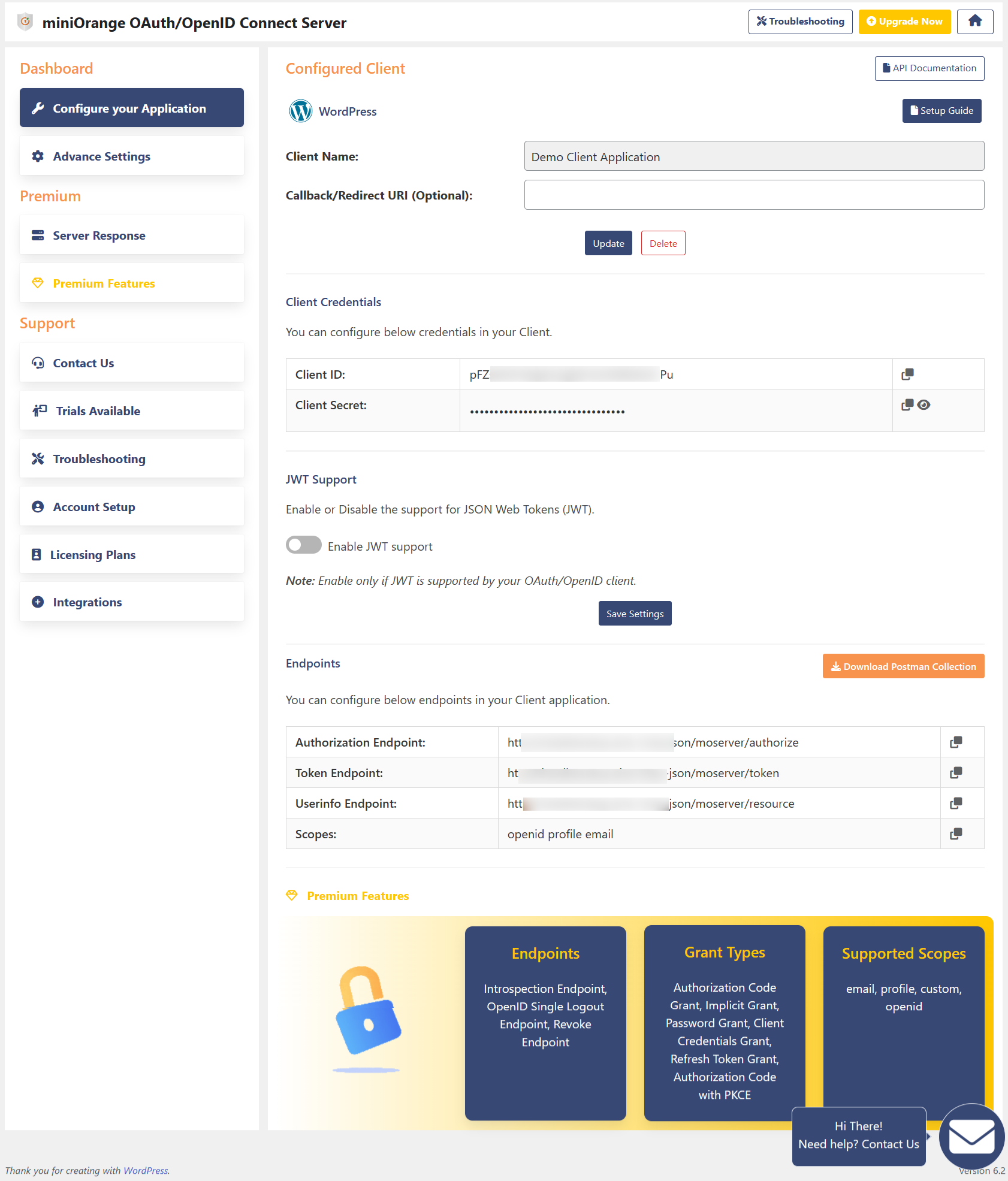
- Server Response: Sends User ID, username, email, first name, last name, display name in the response
- Grant types Supported: Authorization Code grant
- Multi-Site Support: Use the plugin in WordPress Multisite network environment. You can configure individually in all the subsites.
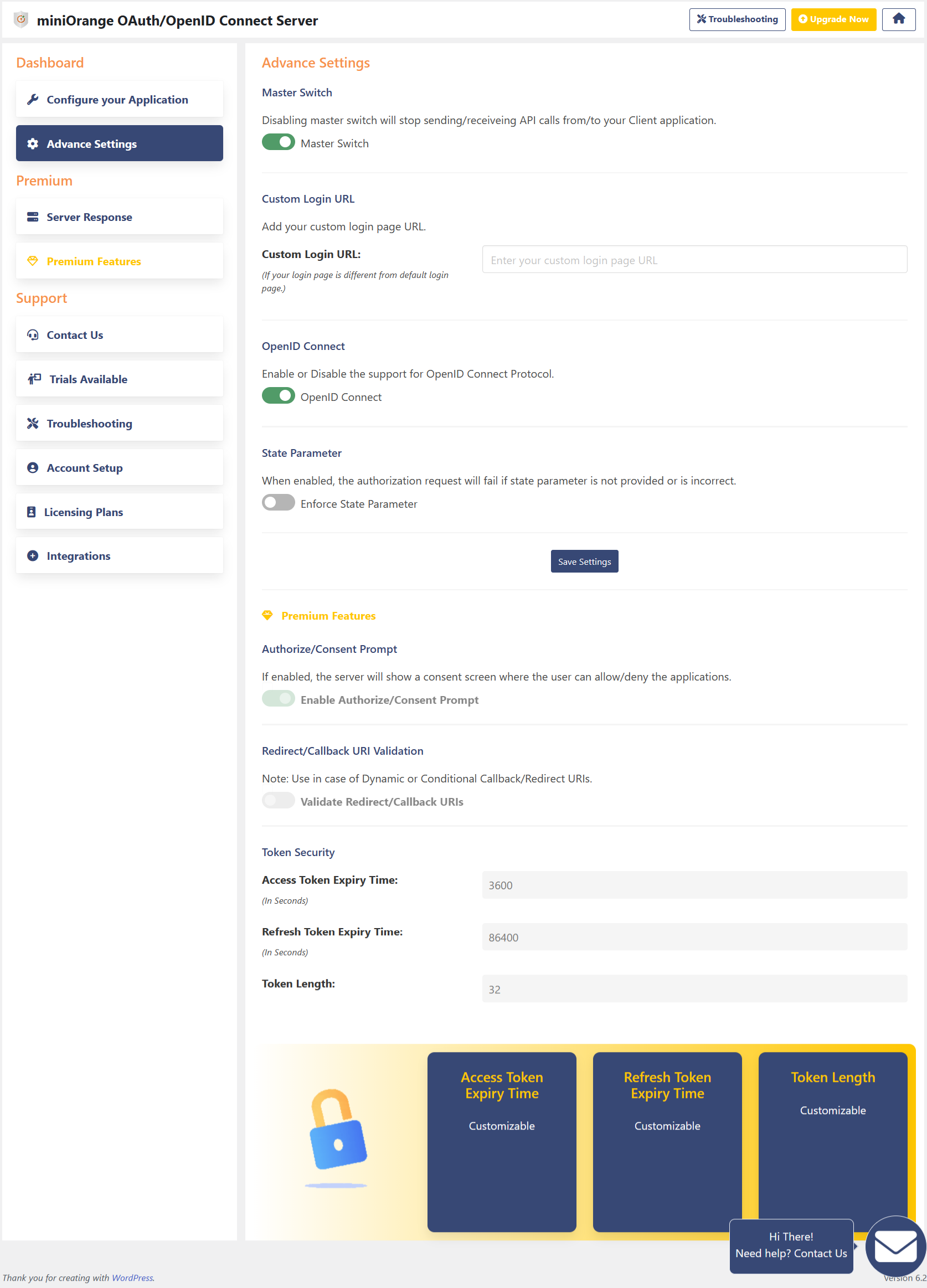
- Master Switch: Block / unblock OAuth API calls between OAuth Clients and Server
- Token Length: Change the access token length
- OAuth API Documentation
- Setup guides to configure the plugin with various OAuth Clients (more coming soon)
WORDPRESS OAUTH / OPENID CONNECT SERVER PREMIUM VERSION FEATURES
- All FREE version features
- Supports Login with WordPress for Multiple Client applications
- Server Response: Sends all the profile attributes along with roles, allows to send custom attributes from usermeta table and also customize the attribute names that need to be sent in server response
- Grant Types Supported: Authorization Code Grant, Implicit Grant, Password Grant, Client Credentials Grant, Refresh Token Grant, Authorization Code grant with PKCE flow
- Token Lifetime: Configure the access token and refresh token expiry time
- Enforce State Parameter: Based on client configuration, you can enable or disable state parameter
- Authorize / Consent prompt: Enable / disable the consent screen
- Redirect / Callback URI Validation: Enable / disable this feature, based on dynamic redirect to a different pages for certain conditions
- JWT Signing Algorithm: Supports signing algorithms HSA and RSA (with dynamic keys for each client setup)
- Additional endpoints: Provides Introspection endpoint, OpenID Connect Single logout endpoint, Revoke endpoint
A grant is a method of acquiring an access token. Deciding which grants to implement depends on the type of client the end user will be using, and the experience you want for your users.
WE SUPPORT FOLLOWING GRANTS:
- Authorization code grant : This code grant is used when there is a need to access the protected resources on behalf of the user on another third party application.
- Implicit grant : This grant relies on resource owner and registration of redirect uri. In authorization code grant users need to ask for authorization and access token each time, but here access token is granted for a particular redirect uri provided by a client using a particular browser.
- Client credential grant : This grant type heads towards specific clients, where access token is obtained by client by only providing client credentials. This grant type is quite confidential.
- Resource owner password credentials grant : This type of grant is used where the resource owner has a trust relationship with the client. Just by using username and password, provided by resource owner authorization and authentication can be achieved.
- Refresh token grant : Access tokens obtained in OAuth flow eventually expire. In this grant type client can refresh his or her access token.
- Authorization code grant with PKCE flow : This grant type is used for public clients like mobile and native apps, Single Page web apps, where there is a risk of client secret being compromised.
REST API AUTHENTICATION
Rest API is very much open to interact. Creating posts, getting information of users and much more is readily available.
It secures unauthorized access to your WordPress sites/pages using our WordPress REST API Authentication plugin .
Screenshots
FAQ
ChangeLog