Check the URL and Redirect it if any XSS Vulnerability found
| Author: | Sami Ahmed Siddiqui (profile at wordpress.org) |
| WordPress version required: | 3.5 |
| WordPress version tested: | 6.0.1 |
| Plugin version: | 2.0.1 |
| Added to WordPress repository: | 23-08-2017 |
| Last updated: | 19-08-2022 |
| Rating, %: | 100 |
| Rated by: | 7 |
| Plugin URI: | https://www.yasglobal.com/web-design-developm... |
| Total downloads: | 50 544 |
| Active installs: | 7 000+ |
 Click to start download |
|
This plugin provides the functionality for Reflected XSS and Self-XSS.
For Reflected XSS, it checks the URL and redirects it if you enabled the Enable Blocking option and URL contains any Vulnerable code in it. It only block some parameters which are not allowed in URL and shown Block Parameters section. You can skip some of the parameters from it if you still like them to be used.
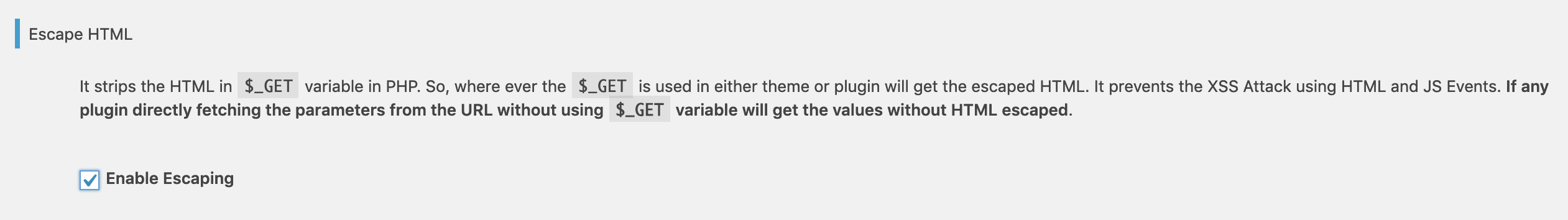
To provide more security, Prevent XSS Vulnerability also escape the HTML in the $_GET parameter which is commonly used to get parameters in PHP from the URL and print them in the HTML. This way, HTML properties will not work if anyone provided it in the URL.
There are many ways by which the plugin can be tested but it may varies for different sites according to their structure and development functionality.
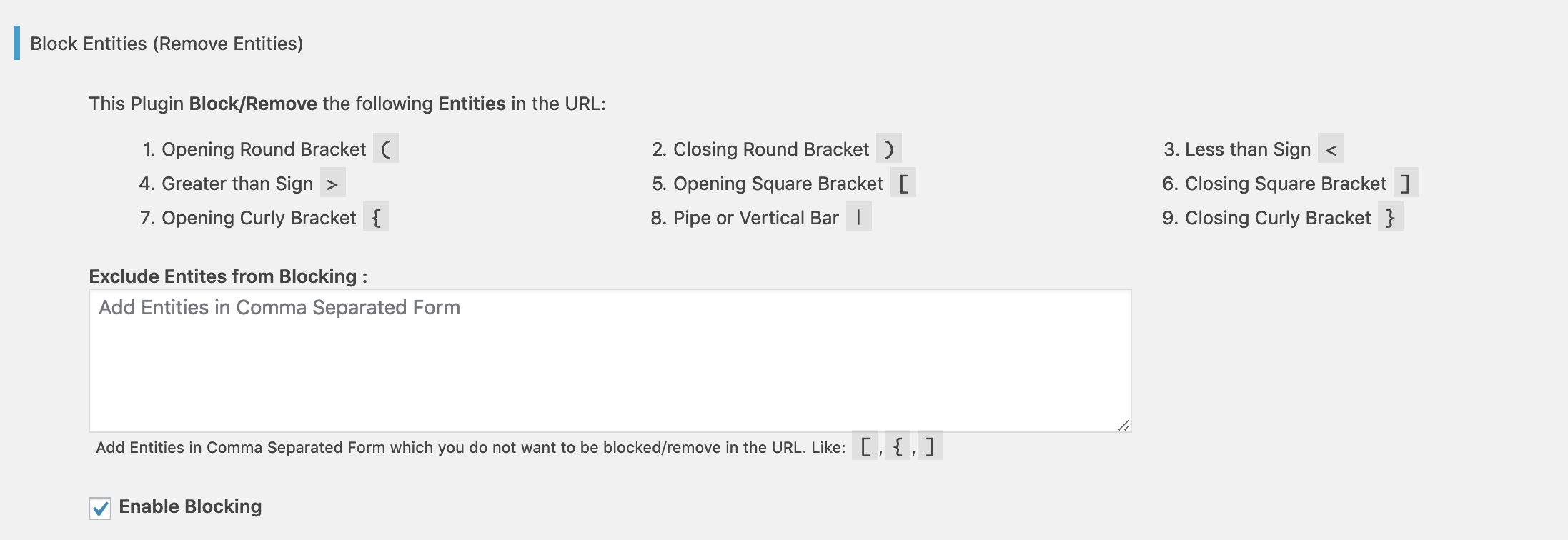
Block Parameters
Prevent XSS Vulnerability block the following parameters in the URL if enabled from the Plugin Settings page.
- Opening Round Bracket
( - Closing Round Bracket
) - Less than Sign
< - Greater than Sign
> - Opening Square Bracket
[ - Closing Square Bracket
] - Opening Curly Bracket
{ - Pipe or Vertical Bar
| - Closing Curly Bracket
}
You can exclude any of the pre-defined parameter(s) or include any other parameter(s) from the Plugin Settings page.
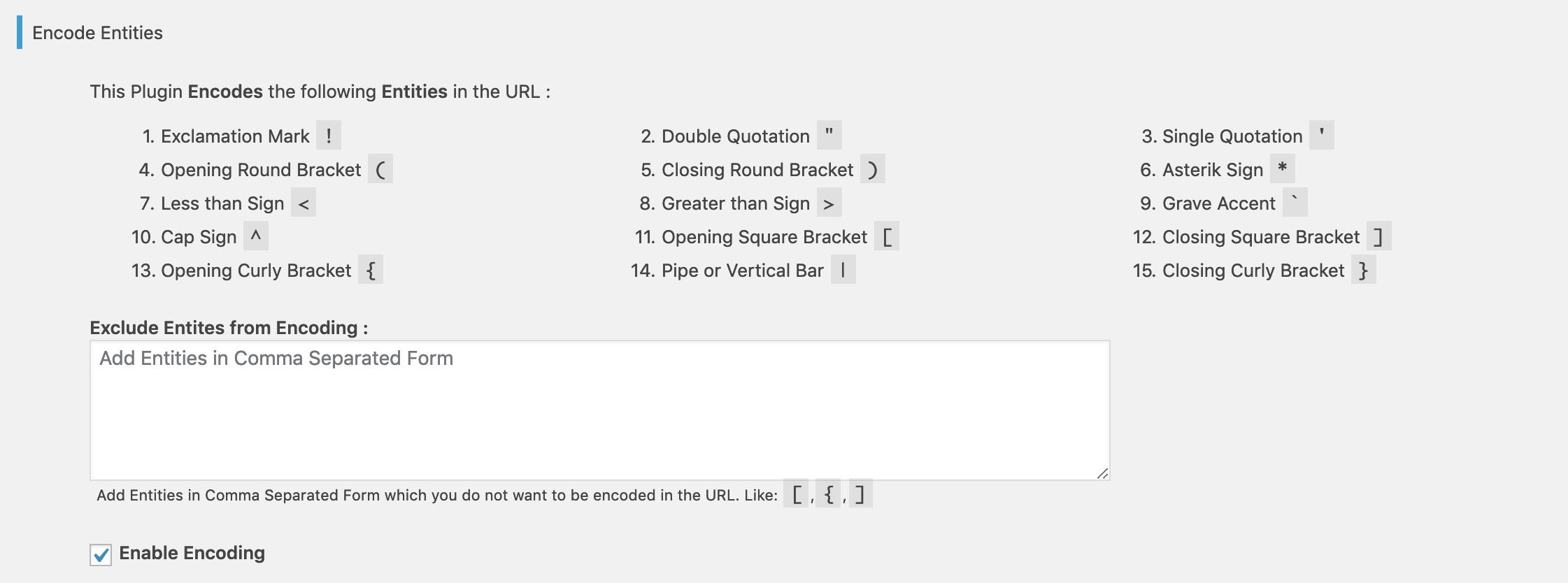
Encode Parameters
Prevent XSS Vulnerability encode the following parameters in the URL if enabled from the Plugin Settings page.
- Exclamation Mark
! - Double Quotation
" - Single Quotation
' - Opening Round Bracket
( - Closing Round Bracket
) - Asterisk Sign
* - Less than Sign
< - Greater than Sign
> - Grave Accent “`
- Cap Sign
^ - Opening Square Bracket
[ - Closing Square Bracket
] - Opening Curly Bracket
{ - Pipe or Vertical Bar
| - Closing Curly Bracket
}
You can exclude any of the pre-defined parameter(s) to being encoded from the Plugin Settings page.
Escape HTML in `$_GET` Variable
Prevent XSS Vulnerability escape HTML in `$_GET` variable. `$_GET` variable is mostly used to put the values in HTML from the URL. This Check is quite useful if your site using/getting anything from the URL and printing it in HTML. It secures your Search and other sections as per your site functionality.
NOTE: Make sure to check your forms after activating the plugin and if you have woocommerce site then please also check the cart and checkout process.
Bug reports
Bug reports for Prevent XSS Vulnerability are welcomed on GitHub. Please note GitHub is not a support forum, and issues that aren’t properly qualified as bugs will be closed.
Screenshots
FAQ
ChangeLog