A feature plugin for core to provide Application Passwords
| Author: | George Stephanis (profile at wordpress.org) |
| WordPress version required: | 4.4 |
| WordPress version tested: | 5.5.5 |
| Plugin version: | 0.1.3 |
| Added to WordPress repository: | 04-02-2016 |
| Last updated: | 07-05-2021
Warning! This plugin has not been updated in over 2 years. It may no longer be maintained or supported and may have compatibility issues when used with more recent versions of WordPress.
|
| Rating, %: | 94 |
| Rated by: | 31 |
| Plugin URI: | https://github.com/WordPress/application-pass... |
| Total downloads: | 342 436 |
| Active installs: | 10 000+ |
 Click to start download |
|
⚠️ IMPORTANT: This plugin has been merged into WordPress core version 5.6 and doesn’t have to be installed separately. View the integration guide →
Use Application Passwords to authenticate users without providing their passwords directly. Instead, a unique password is generated for each application without revealing the user’s main password. Application passwords can be revoked for each application individually.
Important: Application Passwords can be used only for authenticating API requests such as REST API and XML-RPC, and they won’t work for regular site logins.
Contribute
- Translate the plugin into your language.
- Report issues, suggest features and contribute code on GitHub.
Creating Application Password Manually
- Go the User Profile page of the user that you want to generate a new application password for. To do so, click Users on the left side of the WordPress admin, then click on the user that you want to manage.
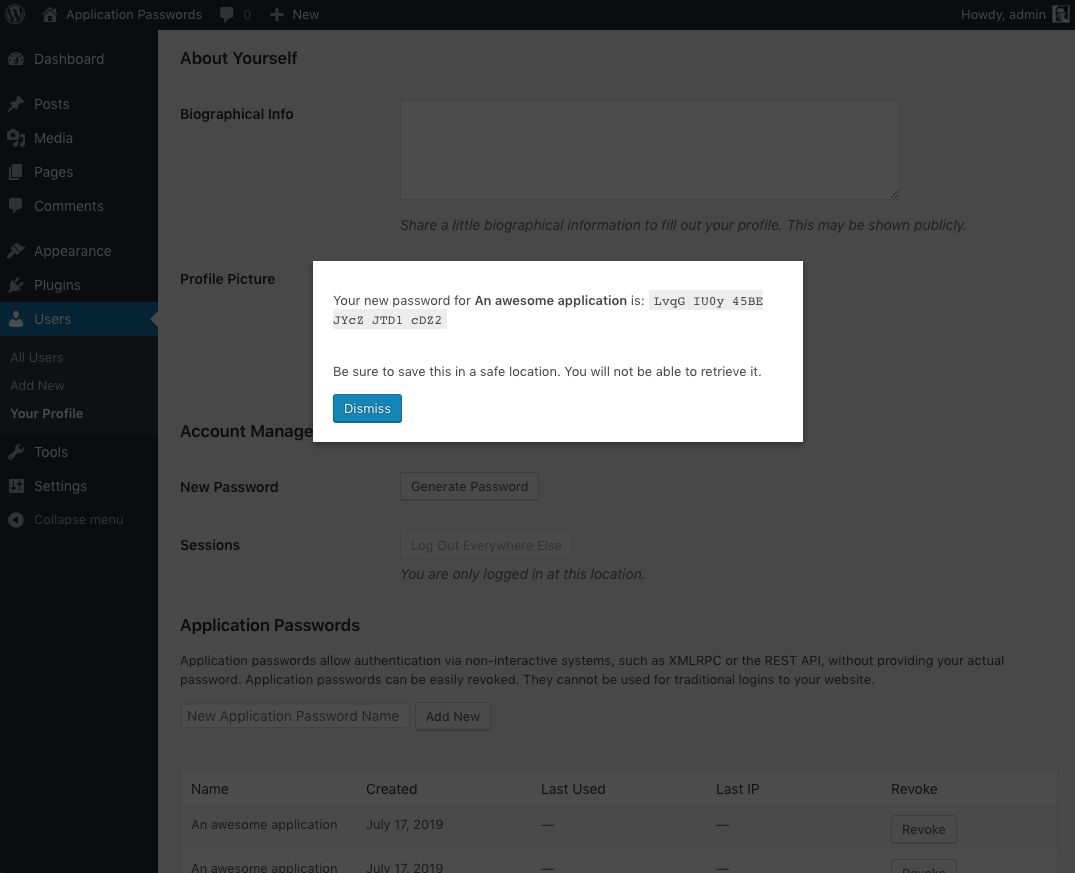
- Scroll down until you see the Application Passwords section. This is typically at the bottom of the page.
- Within the input field, type in a name for your new application password, then click Add New.
Note: The application password name is only used to describe your password for easy management later. It will not affect your password in any way. Be descriptive, as it will lead to easier management if you ever need to change it later. - Once the Add New button is clicked, your new application password will appear. Be sure to keep this somewhere safe, as it will not be displayed to you again. If you lose this password, it cannot be obtained again.
Two Factor Support
Application Passwords can be used together with the Two Factor plugin as long as you bypass the API acccess restrictions added by the Two Factor plugin. Those protections disable API requests with password authentication for users with Two Factor enabled.
Use the two_factor_user_api_login_enable filter to allow API requests authenticated using an application passwords:
add_filter( 'two_factor_user_api_login_enable', function( $enable ) {
// Allow API login when using an application password even with 2fa enabled.
if ( did_action( 'application_password_did_authenticate' ) ) {
return true;
}
return $enable;
} );
This is not required if the user associated with the application password doesn’t have any of the Two Factor methods enabled.
Requesting Password for Application
To request a password for your application, redirect users to:
https://example.com/wp-admin/admin.php?page=auth_app
and use the following GET request parameters to specify:
app_name(required) – The human readable identifier for your app. This will be the name of the generated application password, so structure it like … “WordPress Mobile App on iPhone 12” for uniqueness between multiple versions. If omitted, the user will be required to provide an application name.success_url(recommended) – The URL that you’d like the user to be sent to if they approve the connection. Two GET variables will be appended when they are passed back —user_loginandpassword— these credentials can then be used for API calls. If thesuccess_urlvariable is omitted, a password will be generated and displayed to the user, to manually enter into your application.reject_url(optional) – If included, the user will get sent there if they reject the connection. If omitted, the user will be sent to thesuccess_url, with?success=falseappended to the end. If thesuccess_urlis omitted, the user will be sent to their dashboard.
Testing an Application Password
We use curl to send HTTP requests to the API endpoints in the examples below.
WordPress REST API
Make a REST API call to update a post. Because you are performing a POST request, you will need to authorize the request using your newly created base64 encoded access token. If authorized correctly, you will see the post title update to “New Title.”
curl --user "USERNAME:APPLICATION_PASSWORD" -X POST -d "title=New Title" https://LOCALHOST/wp-json/wp/v2/posts/POST_ID
When running this command, be sure to replace USERNAME and APPLICATION_PASSWORD with your credentials (curl takes care of base64 encoding and setting the Authorization header), LOCALHOST with the hostname of your WordPress installation, and POST_ID with the ID of the post that you want to edit.
XML-RPC
Unlike the WordPress REST API, XML-RPC does not require your username and password to be base64 encoded. Send an XML-RPC request to list all users:
curl -H 'Content-Type: text/xml' -d '<methodCall><methodName>wp.getUsers</methodName><params><param><value>1</value></param><param><value>USERNAME</value></param><param><value>PASSWORD</value></param></params></methodCall>' https://LOCALHOST/xmlrpc.php
In the above example, replace USERNAME with your username, PASSWORD with your new application password, and LOCALHOST with the hostname of your WordPress installation. This should output a response containing all users on your site.
Plugin History
This is a feature plugin that is a spinoff of the main Two-Factor Authentication plugin.
Screenshots
ChangeLog